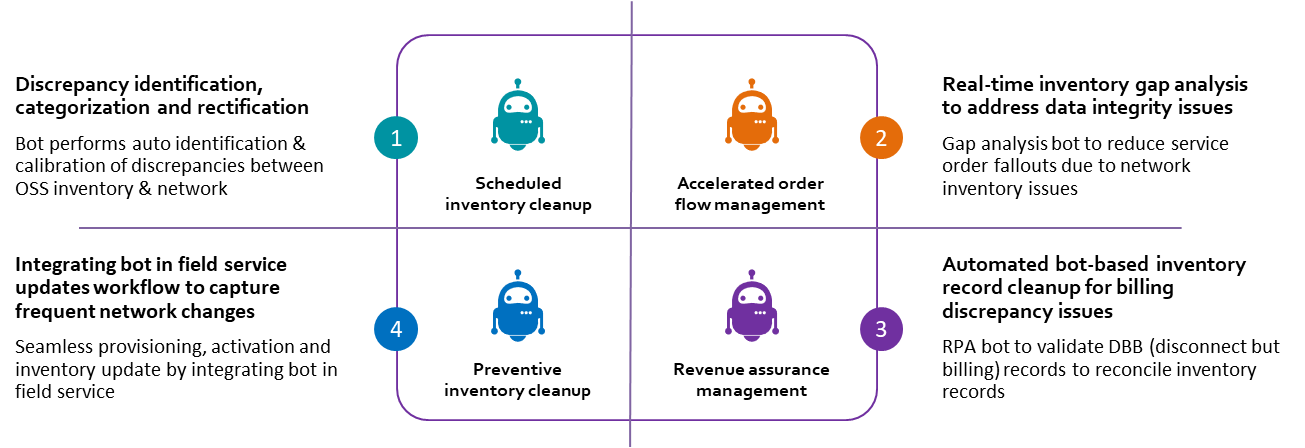
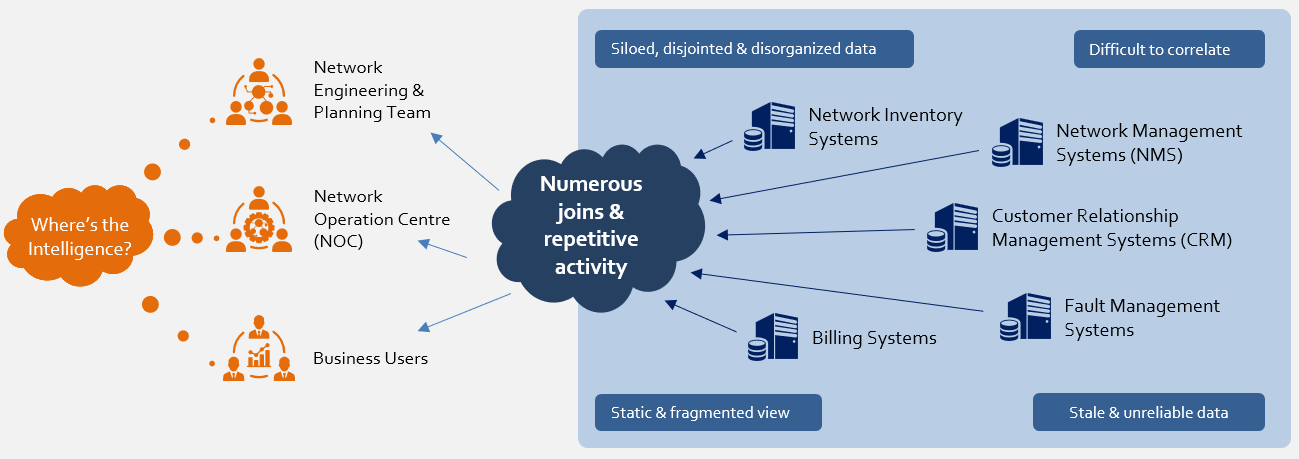
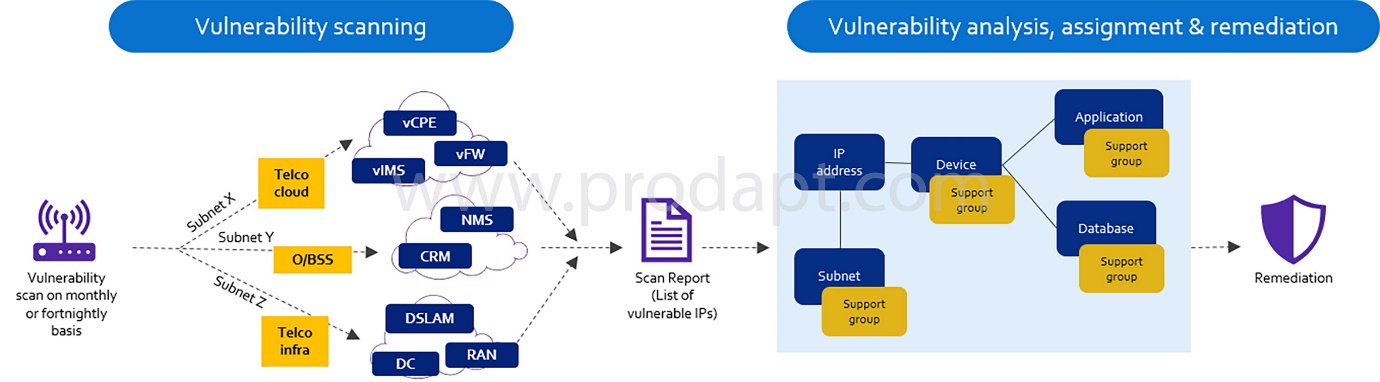
Implement Infrastructure as Code (IaC) to reduce provisioning time by 65%
IT infrastructures are generally imagined as big rooms with huge servers and systems connected with a web of wires. Provisioning of this infrastructure has always been a manual process for the service providers in the connectedness industry, which leads to a lot of accuracy and consistency issues. The advent of cloud computing helped in addressing most of these issues. However, the configuration consistency, manual scalability, and cost issues persisted. Also, deploying complex infrastructure solutions requires considerable effort from cloud architects. These efforts are neither easy to repeat nor modified in a single shot.
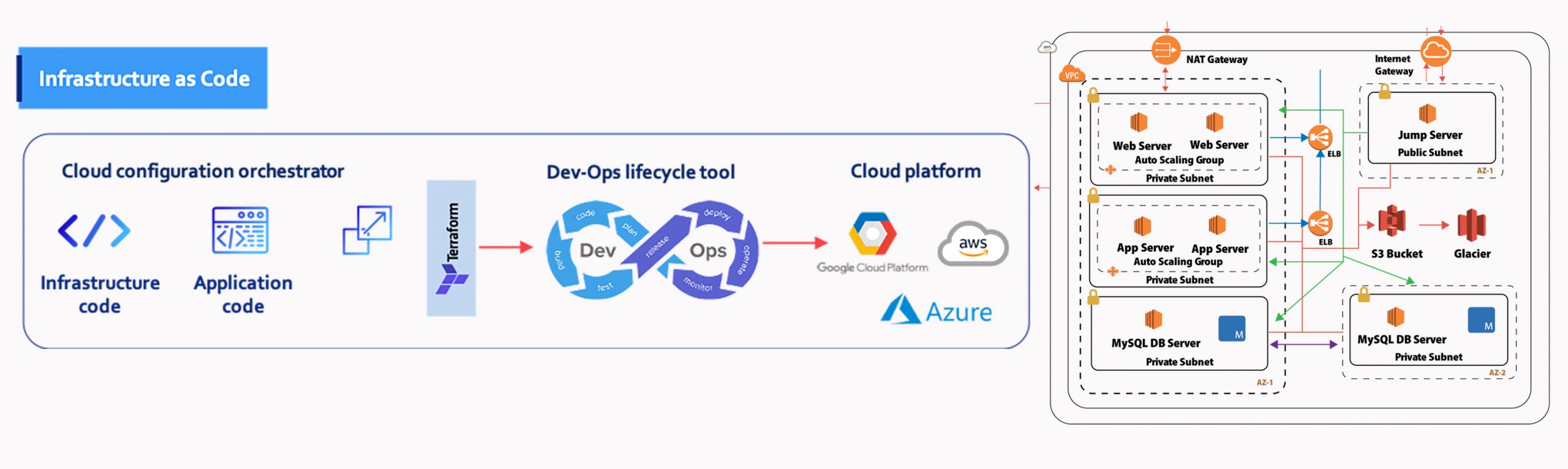
To overcome these challenges, service providers can implement a DevOps Infrastructure as Code (IaC) methodology, which helps in automating the manual, error-prone provisioning tasks. It allows service providers to define the final state infrastructure, application configurations, and scaling policies in a codified way. This, in turn, reduces the dependency on cloud architects and provisioning time significantly.
Infrastructure as Code (IaC) helps the service providers to define the cloud infrastructure, application configurations, and scaling policies in a codified way.